Lawful interception
 For at least five years the stories have been coming about the Israeli company NSO Group. For most people, NSO is not a direct threat. For human rights activists, dissidents, lawyers, politicians, journalists, and others targeted by hostile authoritarian states, however, its elite hackers are dangerous. NSO itself says it supplies lawful interception, and only to governments to help catch terrorists.
For at least five years the stories have been coming about the Israeli company NSO Group. For most people, NSO is not a direct threat. For human rights activists, dissidents, lawyers, politicians, journalists, and others targeted by hostile authoritarian states, however, its elite hackers are dangerous. NSO itself says it supplies lawful interception, and only to governments to help catch terrorists.
Now, finally, someone is taking action. Not, as you might reasonably expect, a democratic government defending human rights, but Apple, which is suing the company on the basis that NSO's exploits cost it resources and technical support. Apple has also alerted targets in Thailand, El Salvador, and Uganda.
On Twitter, intelligence analyst Eric Garland picks over the complaint. Among his more scathing quotes: "Defendants are notorious hackers - amoral 21st century mercenaries who have created highly sophisticated cyber-surveillance machinery that invites routine and flagrant abuse", "[its] practices threaten the rules-based international order", and "NSO's products...permit attacks, including from sovereign governments that pay hundreds of millions of dollars to target and attack a tiny fraction of users with information of particular interest to NSO's customers".
The hidden hero in this story is the Canadian research group calls NSO's work "despotism as a service".
Citizen Lab began highlighting NSO's "lawful intercept" software in 2016, when analysis it conducted with Lookout Security showed that a suspicious SMS message forwarded by UAE-based Ahmed Mansoor contained links belonging to NSO Group's infrastructure. The links would have led Mansoor to a chain of zero-day exploits that would have turned his iPhone 6 into a comprehensive, remotely operated spying device. As Citizen Lab wrote, "Some governments cannot resist the temptation to use such tools against political opponents, journalists, and human rights defenders." It went on to note the absence of human rights policies and due diligence at spyware companies; the economic incentives all align the wrong way. An Android version was found shortly afterwards.
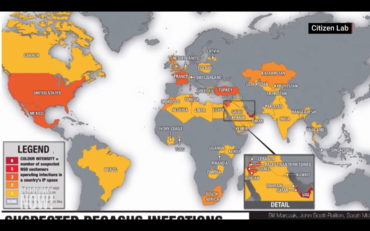
Among the targets Citizen Lab found in 2017: Mexican scientists working on obesity and soda consumption and Amnesty International researchers, In 2018, Citizen Lab reported that Internet scans found 45 countries where Pegasus appeared to be in operation, at least ten of them working cross-border. In 2018, Citizen Lab found Pegasus on the phone of Canadian resident Omar Abdulaziz, a Saudi dissident linked to murdered journalist Jamal Khashoggi. In September 2021, Citizen Lab discovered NSO was using a zero-click, zero-day vulnerability in the image rendering library used in Apple's iMessage to take over targets' iOS, WatchOS, and MacOS devices. Apple patched 1.65 billion products.
Both Privacy International and the Pegasus project, an joint investigation into the company by media outlets including the Guardian and coordinated by Forbidden Stories, have found dozens more examples.
In July 2021, a leaked database of 50,000 phone numbers believed to belong to people of interest to NSO clients since 2016 included human rights activists, business executives, religious figures, academics, journalists, lawyers, and union and government officials around the world. It was not clear if their devices had been hacked. Shortly afterwards, Rappler reported that NSO spyware can successfully infect even the latest, most secure iPhones.
Citizen Lab began tracking litigation and formal complaints against spyware companies in 2018. In a complaint filed in 2019, WhatsApp and Facebook are arguing that NSO and Q Cyber used their servers to distribute malware; on November 8 the US ninth circuit court of appeals has rejected NSO's claim of sovereign immunity, opening the way to discovery.. Privacy International promptly urged the British government to send a clear message, given that NSO's target was a UK-based lawyer challenging the company over human rights violations in Mexico and Saudi Arabia.
Some further background is to be found at Lawfare, where shortly *before* the suit was announced, security expert Stephanie Pell and law professor David Kaye discuss how to regulate spyware. In 2019, Kaye wrote a report calling for a moratorium on the sale and transfer of spyware and noting that its makers "are not subject to any effective global or national control". Kaye proposes adding human rights-based export rules to the Wassenaar Arrangement export controls for conventional arms and dual-use technologies. Using Wassenaar, on November 3 the US Commerce Department recently blacklisted NSO along with fellow Israeli company Candiru, Russian company Positive Technologies, and Singapore-based Computer Security Initiative Consultancy as national security threats. And there are still more, such as the surveillance system sold to Egypt by France-based Thales subsidiary Dassault and Nexa Technologies.
The story proves the point many have made throughout 30 years of fighting for the right to use strong encryption: while governments and their law enforcement agencies insist they need access to keep us safe: there is no magic hole that only "good guys" can use, and any system created to give special access will always end up being abused. We can't rely on the technology companies to defend human rights; that's not in their business model. Governments need to accept and act on the reality that exceptional access for anyone makes everyone everywhere less safe.
Illustrations: Citizen Lab's 2021 map of the distribution of suspected NSO infections (via Democracy Now.
Wendy M. Grossman is the 2013 winner of the Enigma Award. Her Web site has an extensive archive of her books, articles, and music, and an archive of earlier columns in this series. Stories about the border wars between cyberspace and real life are posted occasionally during the week at the net.wars Pinboard - or follow on Twitter.